Outlook
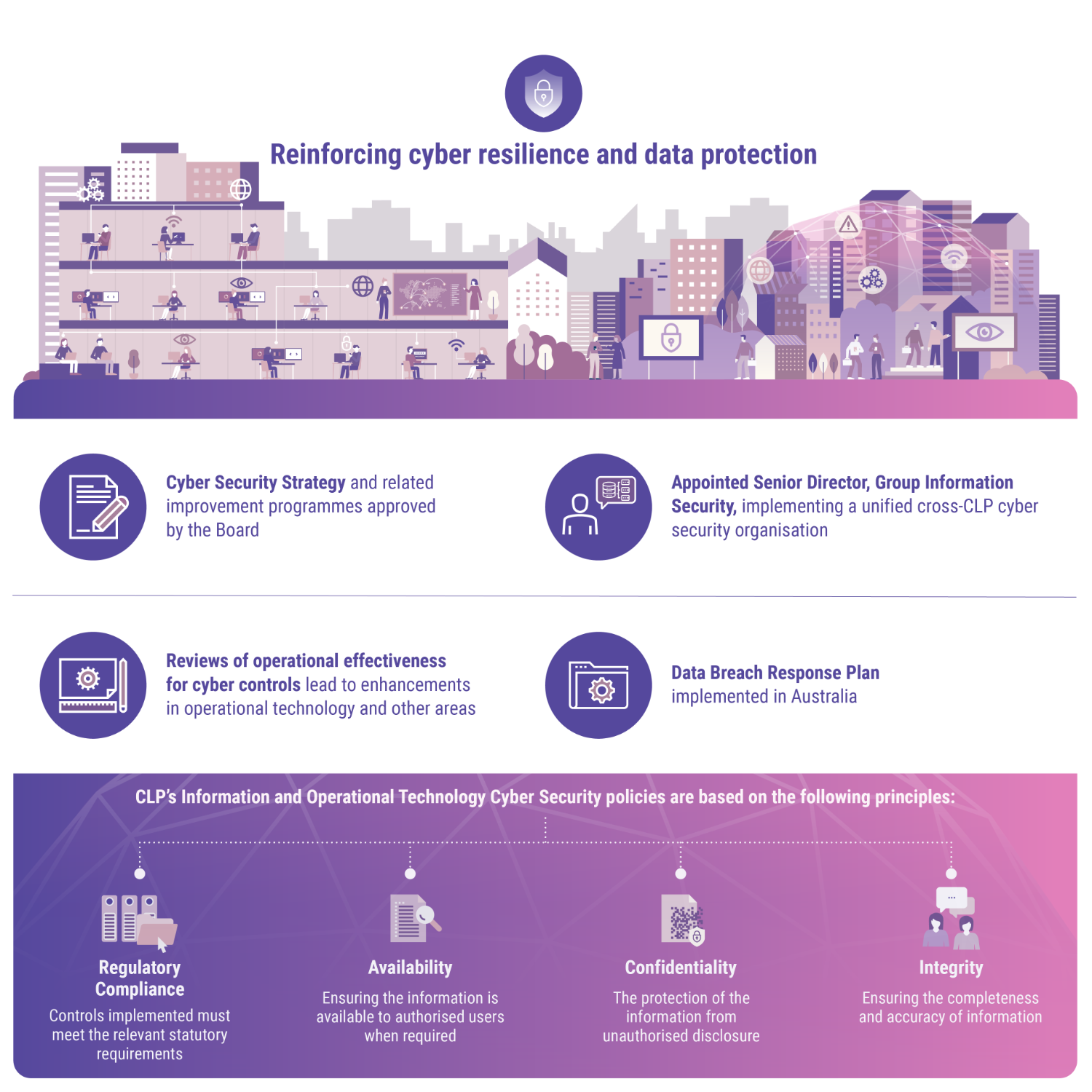
Cyber resilience is especially important for companies like CLP which provide critical infrastructure. A cyber breach could have a significant impact not only on the Company, but also on the environment and the economy at large.
As electric utilities become more connected and decentralised, the exposure to malicious attack cannot be eliminated. It is only by embedding cyber security into the mindset of all employees and their daily tasks, and continually enhancing organisational capacity that a company can defend itself or respond promptly should an attack occur.
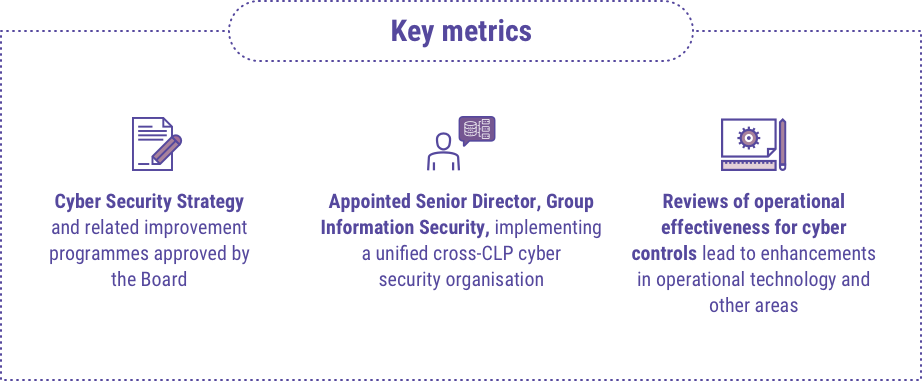
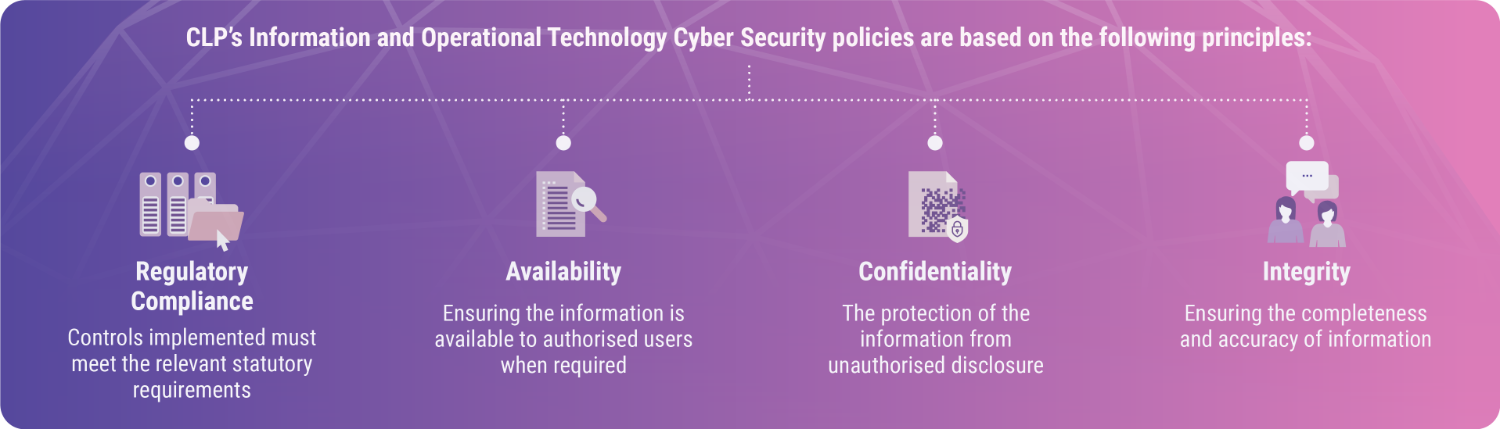
CLP has been making good progress in building up internal expertise and a strong organisational awareness of the importance of cyber security. As the business evolves and the systems that underlie it change, new vulnerabilities arise.
Going forward CLP will be implementing a range of further cyber security measures at a level of people, process and technology, with the Audit & Risk Committee maintaining an oversight. The Group will also continue its awareness raising and emergency preparedness initiatives, so that employees remain continually vigilant.